An especially active month for security patch releases and activity on Quasar-Sec
Since it has been a rather demanding month, we will focus on the most significant patches released during this period, detailing their vulnerabilities (CVE), a brief description of each, and their severity scores (CVSS):
🔴 Software and Vulnerabilities
- Google Chrome (This is a top of last post)
- CVE-2024-4671: Image rendering vulnerability. CVSS: 7.8
- CVE-2024-4761: Memory management flaw. CVSS: 6.5
- CVE-2024-4947: Remote code execution. CVSS: 9.1
- CVE-2024-5274: Vulnerability in JS V8. CVSS: 8.2
- Google Chrome (This is a top of last post)
- WinRAR
- CVE-2023-38831: Malicious code execution. CVSS: 7.2
- Apache Flink
- CVE-2020-28188: Authentication flaw. CVSS: 6.9
- CVE-2020-17519: Deserialization vulnerability. CVSS: 5.4
- CVE-2020-29227: Sensitive information leak. CVSS: 7.3
- WinRAR
- MS Exchange (ProxyShell Flaws)
- CVE-2021-34473: Remote code execution. CVSS: 9.8
- CVE-2021-34523: Privilege escalation. CVSS: 8.8
- CVE-2021-31207: Authentication bypass vulnerability. CVSS: 8.0
- MS Exchange (ProxyShell Flaws)
- Veeam Backup
- CVE-2024-29849: Input validation flaw. CVSS: 7.5
- CVE-2024-29850: Authentication vulnerability. CVSS: 6.7
- CVE-2024-29851: Arbitrary code execution. CVSS: 5.8
- CVE-2024-29852: Sensitive information leak. CVSS: 7.9
- Veeam Backup
- D-Link Routers
- CVE-2014-100005: Remote command execution. CVSS: 9.3
- CVE-2021-40655: Authentication flaw. CVSS: 8.6
- D-Link Routers
- Microsoft Patches (This month released 61 patches plus several affecting shared libraries in third-party products)
- CVE-2024-22845: Windows Kernel vulnerability. CVSS: 7.6
- CVE-2024-22846: Hyper-V flaw. CVSS: 8.1
- CVE-2024-22847: Remote code execution. CVSS: 7.4
- CVE-2024-22848: Privilege escalation in SMB. CVSS: 8.2
- CVE-2024-22849: Azure authentication flaw. CVSS: 7.9
- Microsoft Patches (This month released 61 patches plus several affecting shared libraries in third-party products)
- VMWare
- CVE-2024-22267: Remote code execution. CVSS: 6.4
- CVE-2024-22268: Vulnerability in VMware Tools. CVSS: 7.1
- CVE-2024-22269: Privilege escalation. CVSS: 8.3
- CVE-2024-22670: SSO authentication flaw. CVSS: 9.0
- VMWare
- Cacti
- CVE-2024-25641: SQL injection. CVSS: 6.5
- CVE-2024-29895: Authentication flaw. CVSS: 7.7
- CVE-2024-31445: Remote code execution. CVSS: 8.1
- CVE-2024-31459: Sensitive information leak. CVSS: 6.9
- Cacti
- F5 Next Central Manager
- CVE-2024-21793: Session management vulnerability. CVSS: 8.9
- CVE-2024-26026: Remote command execution. CVSS: 7.8
- F5 Next Central Manager
- ArubaOS
- CVE-2024-26304: Authentication flaw. CVSS: 6.2
- CVE-2024-26305: Bypass vulnerability. CVSS: 7.1
- CVE-2024-33511: Remote code execution. CVSS: 8.4
- CVE-2024-33512: Privilege escalation. CVSS: 7.5
- ArubaOS
- GitLab
- CVE-2023-7028: Information leak. CVSS: 7.4
- CVE-2023-4812: Authentication flaw. CVSS: 6.1
- CVE-2023-6955: Remote code execution. CVSS: 8.2
- CVE-2023-2030: Deserialization vulnerability. CVSS: 7.9
- GitLab
- Git
- CVE-2024-32002: Authentication flaw. CVSS: 7.3
- CVE-2024-32004: Remote code execution. CVSS: 6.8
- CVE-2024-32465: Vulnerabilidad de bypass. CVSS: 8.0
- CVE-2024-32020: Privilege escalation. CVSS: 7.7
- CVE-2024-32021: Sensitive information leak. CVSS: 6.5
- Git
- WordPress
- CVE-2024-27956: SQL injection vulnerability. CVSS: 8.1
- WordPress
Impact of Vulnerabilities
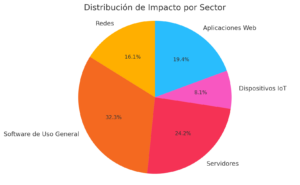
Distribution over Areas
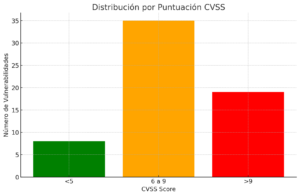
Distribution by CVSS Score
Summary
The number of patches released in May 2024 underscores the importance of keeping all systems up to date, as each of these vulnerabilities represents a potential significant risk, and their mitigation should be a priority for any organization using these products.
It is clear that there are CVEs accompanying products for years, as you can see, some CVEs date back to 2020... (even one from 2014 related to D-Link (https://nvd.nist.gov/vuln/detail/CVE-2014-100005) which affects an EOL product that is still in production, such as the widely used D-Link DIR-600) and today, they are still potentially exploitable.
At Quasar-Sec, as vendors release patches and updates, combined with real-time readings from the scanners we have at our disposal, we strive to implement the best strategy to patch the infrastructure 100% with minimal impact.
